SVTI_VPN
SVTI 实验
SVTI配置被运用于站点到站点的连接(L2LVPN),对于VTI接口,可以控制明文的特性应该
被配置到VTI接口上。SVTI相对于传统crypto map配置的优势在于可以在隧道口上运用动态路由协
议,并且不需要那额外的4字节GRE头部(GRE over IPSec),因此降低了发送加密数据的带宽。当
我们使用IPSec VTI技术,我们可以对明文和加密后的流量分开运用NAT,ACL和QoS等特性。
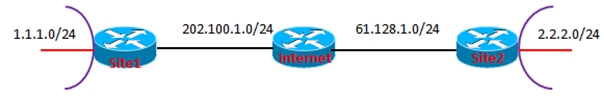
Site 1:
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
crypto isakmp policy 100
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 61.128.1.1
!
!
crypto ipsec transform-set myset esp-3des esp-sha-hmac
!
crypto ipsec profile ipsecprof
set transform-set myset
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface Tunnel0
ip address 172.16.1.1 255.255.255.0
tunnel source FastEthernet0/0
tunnel destination 61.128.1.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile ipsecprof
!
router ospf 100
log-adjacency-changes
network 1.1.1.0 0.0.0.255 area 0
network 172.16.1.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 202.100.1.10
Internet:
interface FastEthernet0/0
ip address 202.100.1.10 255.255.255.0
!
interface FastEthernet0/1
ip address 61.128.1.10 255.255.255.0
Site2:
interface FastEthernet0/1
ip address 61.128.1.1 255.255.255.0
!
interface Loopback0
ip address 2.2.2.2 255.255.255.0
!
crypto isakmp policy 100
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 202.100.1.1
!
!
crypto ipsec transform-set myset esp-3des esp-sha-hmac
!
crypto ipsec profile ipsecprof
set transform-set myset
!
interface Tunnel0
ip address 172.16.1.2 255.255.255.0
tunnel source FastEthernet0/1
tunnel destination 202.100.1.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile ipsecprof
!
router ospf 100
log-adjacency-changes
network 2.2.2.0 0.0.0.255 area 0
network 172.16.1.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 61.128.1.10
测试:
Site1#ping 172.16.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 156/172/204 ms
Site1#show ip route ospf
2.0.0.0/32 is subnetted, 1 subnets
O 2.2.2.2 [110/11112] via 172.16.1.2, 00:12:33, Tunnel0
Site1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
61.128.1.1 202.100.1.1 QM_IDLE 1002 0 ACTIVE
Site1#show crypto engine connections active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
1 Tu0 IPsec 3DES+SHA 0 104 202.100.1.1
2 Tu0 IPsec 3DES+SHA 105 0 202.100.1.1
1002 Tu0 IKE SHA+3DES 0 0 202.100.1.1
Site1#ping 2.2.2.2 source lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Site1#show crypto session
Crypto session current status
Interface: Tunnel0
Session status: UP-ACTIVE
Peer: 61.128.1.1 port 500
IKE SA: local 202.100.1.1/500 remote 61.128.1.1/500 Active
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
本文出自 “优乐美” 博客,请务必保留此出处http://youlemei.blog.51cto.com/2294538/1654775
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。